- Cloud Security Lab a Week (S.L.A.W)
- Posts
- Enable Whichever Version of Security Hub AWS is Supporting These Days
Enable Whichever Version of Security Hub AWS is Supporting These Days
Security Hub is Amazon's built-in CSPM and... other stuff... and... AWS keeps changing it and is in the middle of a major transition. We'll turn it on and see what we get!
CloudSLAW is, and always will be, free. But to help cover costs and keep the content up to date we have an optional Patreon. For $10 per month you get access to our support Discord, office hours, exclusive subscriber content (not labs — those are free — just extras) and more. Check it out!
Prerequisites
The target environment configured in our second Prowler lab.
Our first Security Hub lab, which delegated administration to our SecurityAudit account.
The Lesson
Okay, this is the weirdest lab I’ve built yet. Why? Because I have absolutely no idea how long it will last or what things will look like when you log in. Sure, I try to keep these things updated, but I’m JUST ONE PERSON, and some things change darn quickly in the cloud.
Here’s the TL;DR: Security Hub is Amazon’s built-in security center, and it included CSPM capabilities. But AWS recently split out the non-CSPM parts, named them all Security Hub, renamed the old Security Hub “Security Hub CSPM”, and has said more changes are coming since the new version is only in public preview, so… YOLO!
The Curious Case of Two Security Hubs
Security Hub CSPM is what you're probably thinking of when someone says "Security Hub," if you laid hands on AWS before this change. It runs all those security standards checks, compliance frameworks, and best practice assessments. This is the part that competes with tools like Prowler, which we covered in the last lab. Security Hub CSPM generates findings about misconfigurations, compliance violations, and security gaps.
The "new" Security Hub (which is still in public preview as I write this, but will probably reach general availability soon) is actually a meta-layer that sits on top. Think of it as a security data aggregator and correlation engine. It takes findings from Security Hub CSPM, but also pulls in alerts and findings from GuardDuty, Inspector, Macie, and other AWS security services. Then it correlates all that data, reduces noise, and helps you prioritize what actually matters.
I’ll let AWS marketing do the writing for me: “Security Hub is a unified cloud security solution that prioritizes your critical security issues and helps you respond at scale. Security Hub detects security issues by automatically correlating and enriching security signals from multiple sources, such as posture management, vulnerability management (Amazon Inspector), sensitive data (Amazon Macie), and threat detection (Amazon GuardDuty). … Through intuitive visualizations, Security Hub transforms complex security signals into actionable insights…”
Here's the flow: Security Hub CSPM checks your environment and generates findings → those findings feed into Security Hub → Security Hub correlates them with other security data (GuardDuty, Access Analyzer, Inspector, etc.) → you get a prioritized, deduplicated view of what needs attention.
Now I know you are asking yourself, “didn’t Security Hub always aggregate findings from other services?” Yep. But … it didn’t really do any fancy correlation, so Security Hub wasn’t very competitive with other Cloud Service Provider (CSP) native security tools — like Defender for Cloud and the Google Security Command Center.
Now, about those costs I mentioned. Security Hub CSPM relies heavily on AWS Config to do its job. Config is what actually tracks the state of your resources and detects changes. Some checks happen in real time when resources change, while others run on a schedule. The problem? Config ain’t cheap, so we can’t (yet) just turn on all of Security Hub + Security Hub CSPM without keeping an eye on our bill.
New CSPM, Who Dis?
Although I expect Security Hub to change significantly as it reaches general release and continues to evolve, for educational purposes this new version offers more baseline CSPM capabilities we can use to expand our knowledge:
Inventory: While Security Hub doesn’t offer a full and complete cross-account inventory, it does aggregate its inventory for covered resources — the big ones like EC2 instances and Lambda functions.
Findings: Similar to our Prowler findings, these cover CSPM results (misconfigurations), but also any findings from other tools, such as a vulnerability detected by Inspector (a vulnerability scanner which we haven’t used yet). This starts sounding more like a CNAPP (Cloud Native Application Protection Platform): it can combine management plane misconfigurations with vulnerability info.
Correlation: Combine different sources so I mostly only need to look in one place to figure out what’s going on. This ties tightly into the Inventory (resource) view so I can see misconfigurations, GuardDuty alerts, and more without bouncing into 5 tools.
Exposure and Attack Graph: Exposure findings are higher-priority issues along the lines of, “Oh crap, that is public.” Is something misconfigured, reachable, and/or vulnerable? The attack graph then shows you visually how it might be exploited. It’s eye candy, but who doesn’t love candy?
Automation: Mostly this is “create a ticket somewhere for someone to fix this thing” or “write stupidly complex EventBridge-Lambda-based autoremediations like that insane dude who runs the coleslaw newsletter.”
All of these capabilities (and more) are available in major third-party CSPM/CNAPP tools. They tend to have much more robust capabilities in terms of what they look for, compliance and security standards they support, report generation, filtering and organization of findings, etc. But it’s nice to see AWS building more of this natively, and it works well for us to take our learning to the next level.
Remember, my advice is to turn on your CSPM on day one. We only waited this long to cover the tools in labs because I wanted to give you a solid baseline of security knowledge first.
Key Lesson Points
Modern CSPM tools (many of which are full CNAPP tools) do more than just find basic misconfigurations. They correlate a wide range of security telemetry to help identify and remediate issues.
Security Hub is Amazon’s latest security center, with core CNAPP capabilities to aggregate findings from multiple sources, including workload security scans.
Security Hub CSPM is the “old” Security Hub, and is now the feature that only handles management plane misconfigurations and compliance. It feeds its results into the new Security Hub.
The Lab
🚨 WARNING WARNING WARNING!!!!! 🚨
Do not forget to shut everything down when your are done. Also, you will get possibly thousands of emails as Security Hub finds things. To shut down, you will need to:
Disable Config
Disable Security Hub
Disable Security Hub CSPM (Security Standards)
Otherwise your bill will go up. And honestly, it ain’t worth it for how little you’ll learn. Heck, feel free to just read this lab and skip the hands-on… I won’t be offended. YOU HAVE BEEN WARNED!
This lab will be outdated pretty quickly. The core principles will be the same, but not the details. I fully intend to update this after the next big AWS update.
As I warned, this lab is a bit… rough around the edges. Aside from the AWS issues, I also managed to make a change in my account that I failed to record, and can’t go back and reset. We will:
Update delegated administration for Security Hub
Enable Security Hub
Enable a Security Standard in Security Hub CSPM
Enable Config
Regret our life decisions
Video Walkthrough
Step by Step
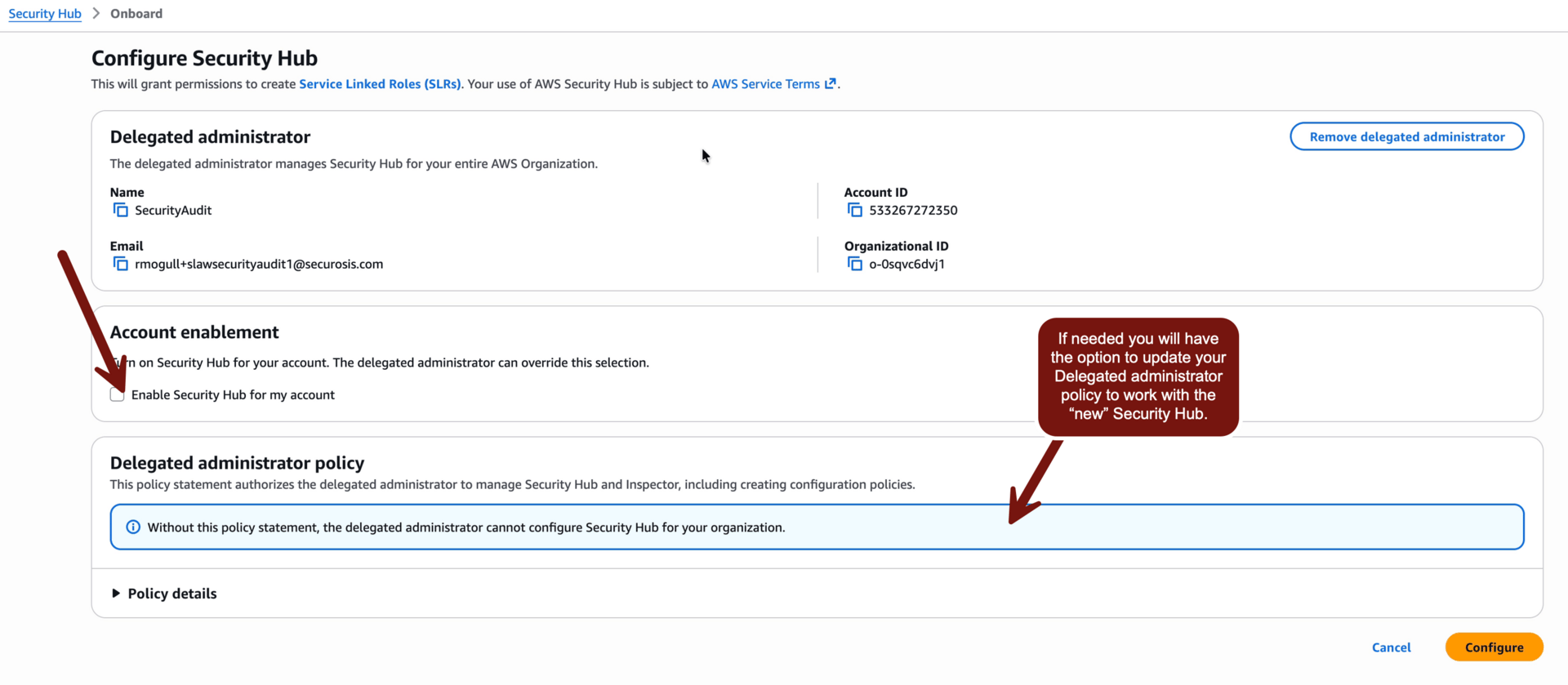
First we need to update our delegated administration policy. THIS MAY BE DIFFERENT depending on when you finished our first Security Hub lab (since you might already be on the new policy). Start in your Sign-in portal > CloudSLAW > AdministratorAccess > Security Hub (remember, NOT Security Hub CSPM — and don’t blame me!). Then click Get Started:
This is where things may get weird. You may need to update your delegated administrator policy, or you might be fine and just need to Enable Security Hub for my account. This is due to the transition. You are a pro now, so figure it out. Then Configure. Here was mine:
Now we need to get Config up and running, since that what Security Hub CSPM currently relies on to get its… configuration information. Since we are already in our management account we can do this with CloudFormation > StackSets > Create stack:
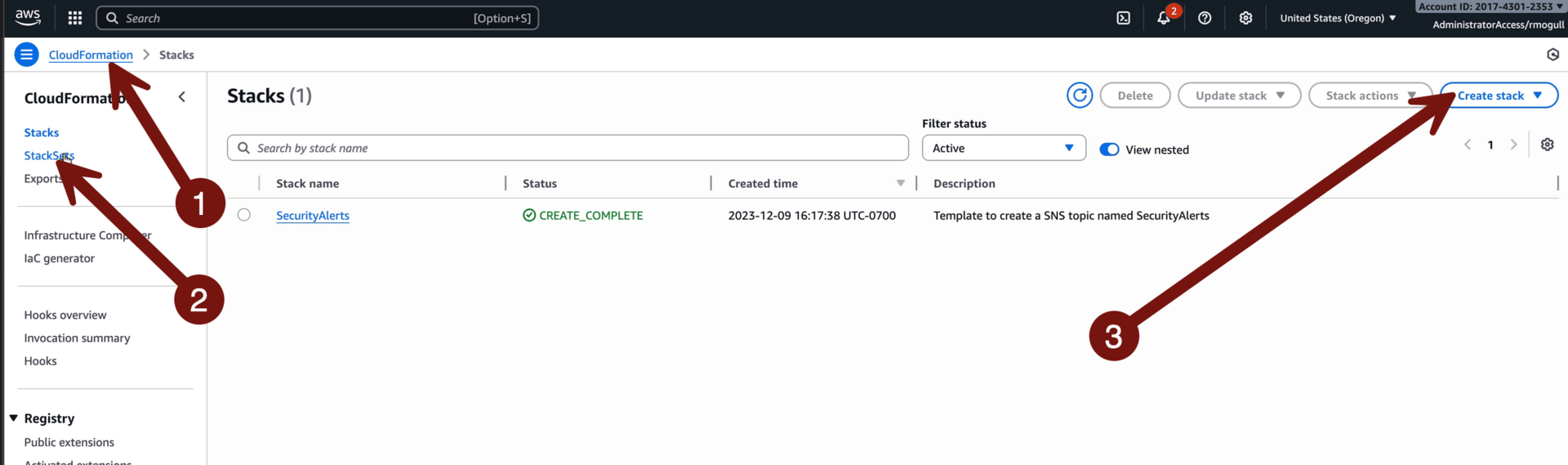
You’ve done this a lot, so here are the settings to change as you walk through the screens:
Create stack set
Use the template: https://cloudslaw.s3-us-west-2.amazonaws.com/lab67.template
Name: “Config”
Deploy new stacks
Deploy to organization
Specify regions us-west-2 and us-east-1
Max concurrent accounts: 10
Failure tolerance: 9
Submit and wait until it’s Succeeded
Exit the management account (close the tab)
Okay, now let’s go to Sign in portal > SecurityAudit > Administrator Access > Security Hub > Getting started (yes, again) > Enable Security Hub:

You can see the four “feeder” services that fuel Security Hub here. Including… Security Hub (CSPM). We already have GuardDuty running, and ‘sorta’ Security Hub CSPM. Depending on the state of this lab, you likely enabled it but without any Security Standards enabled (so it isn’t looking for much) since we didn’t want to run Config. Skip past this for now and Go to Security Hub.

Next we want to set Security Hub to aggregate all findings to our current region. You’ll need to go to Settings > General > Cross-Region aggregation > US West (Oregon) and then also select US East Virginia, then Save:

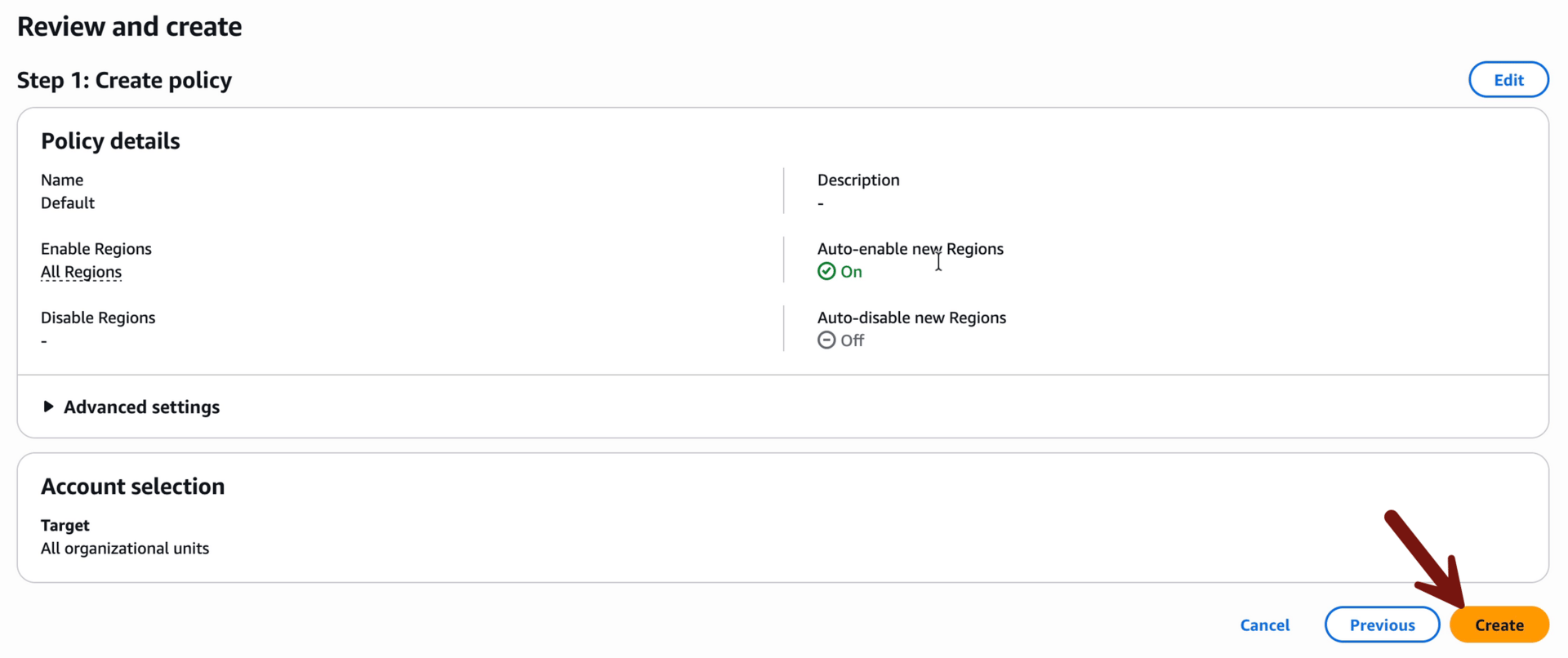
Right now this only has Security Hub running in this one account. We need to enable it for our entire organization so go to Configurations > Policies > Create policy:
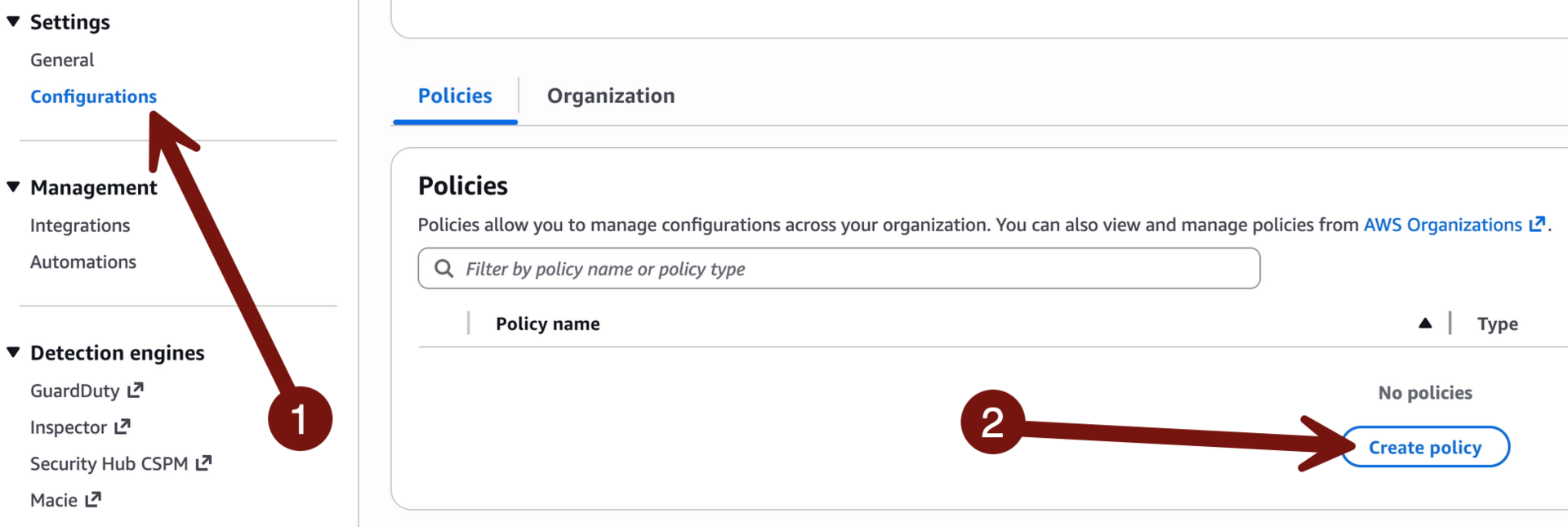
Name: Default
Enable all regions
Scroll to the bottom and click Next, then Create:
🚨 WARNING WARNING WARNING!!!!! 🚨
We are perilously close to the step that will flood your inbox with thousands of emails!
Why? Because we previously set up an EventBridge rule to forward all Security Hub alerts to our email.
You can turn this off. Just go to EventBridge > Rules > SecurityHubAlerts > check the circle, and Disable
Even without Security Hub CSPM fully enabled, findings will start showing up. Most of them are warnings related to not having all the AWS services turned on.
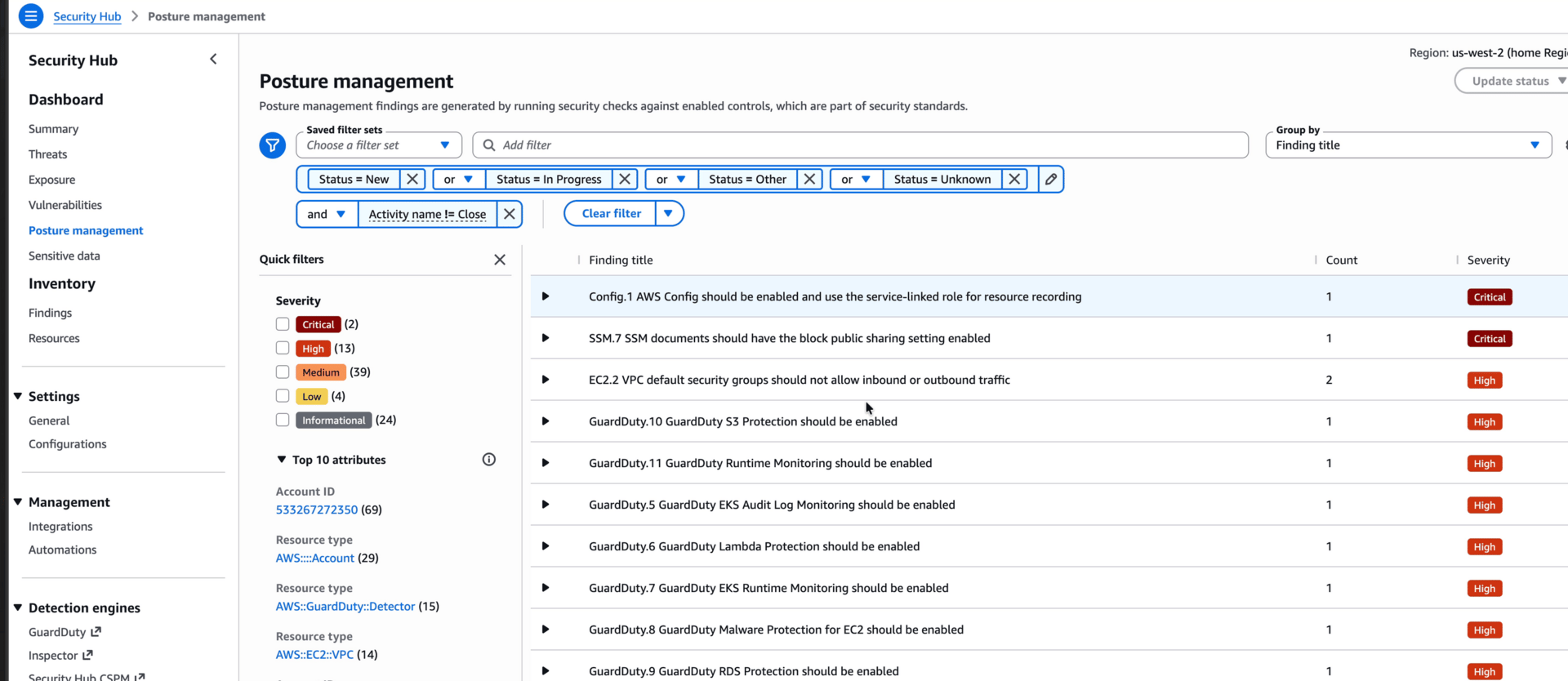
You can already see the problem with CSPM. As important and powerful as it is, basically every tool generates a ton of findings that may or may not matter. In fact, this is why the new Security Hub exists! As you’ll see in a second; while it takes all these feeds it tries to aggregate, correlate, and prioritize.
How well does it work? I don’t know for sure yet, since I’m very early in my testing.
Let’s finish turning on posture checks so we get more information and can compare it more directly to other tools, like Prowler. Go to Detection engines > Security Hub CSPM, which will pop open another window.

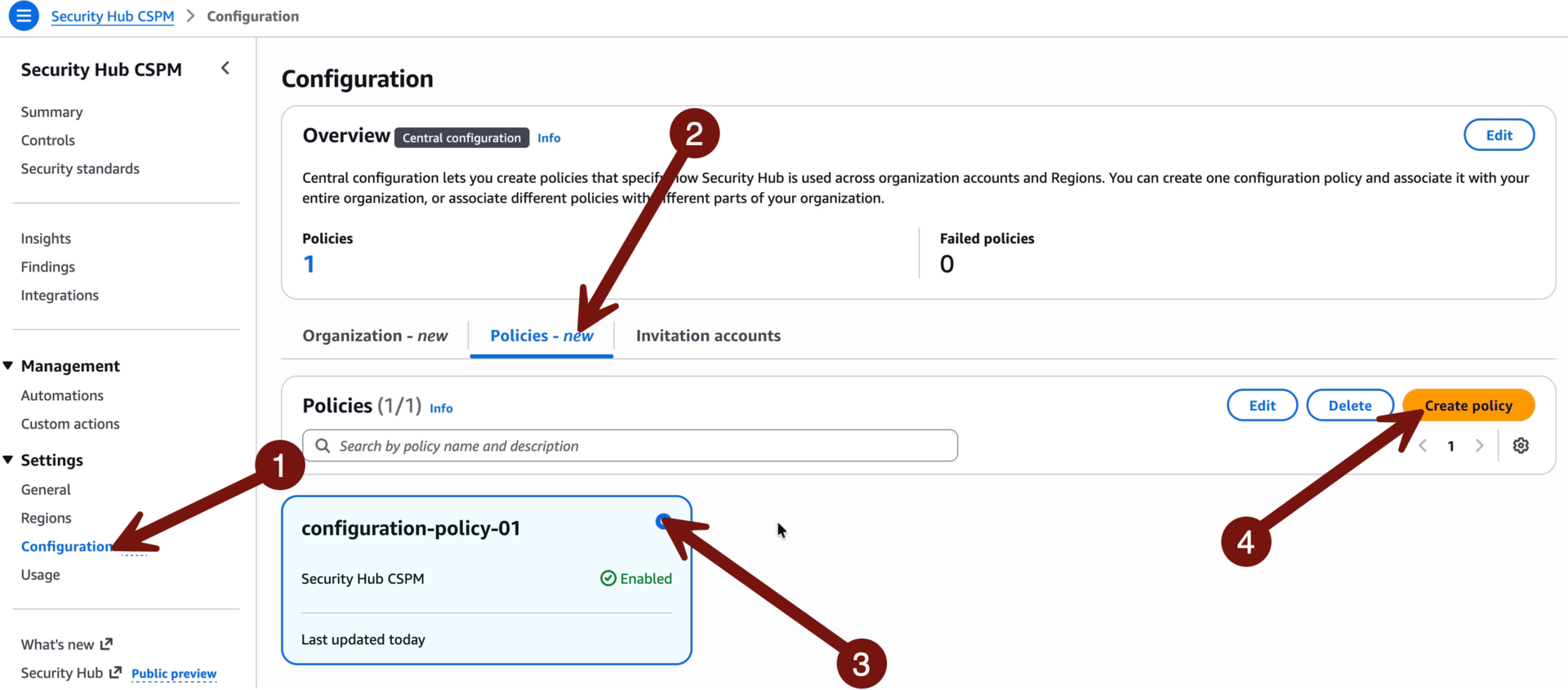
To enable CSPM for our entire organization we need to use a Policy. Go to Configuration > Policies > check the default one already there > Edit (If you don’t see one, go with Create and use the same settings):
Enable AWS Foundational Security Best Practices:
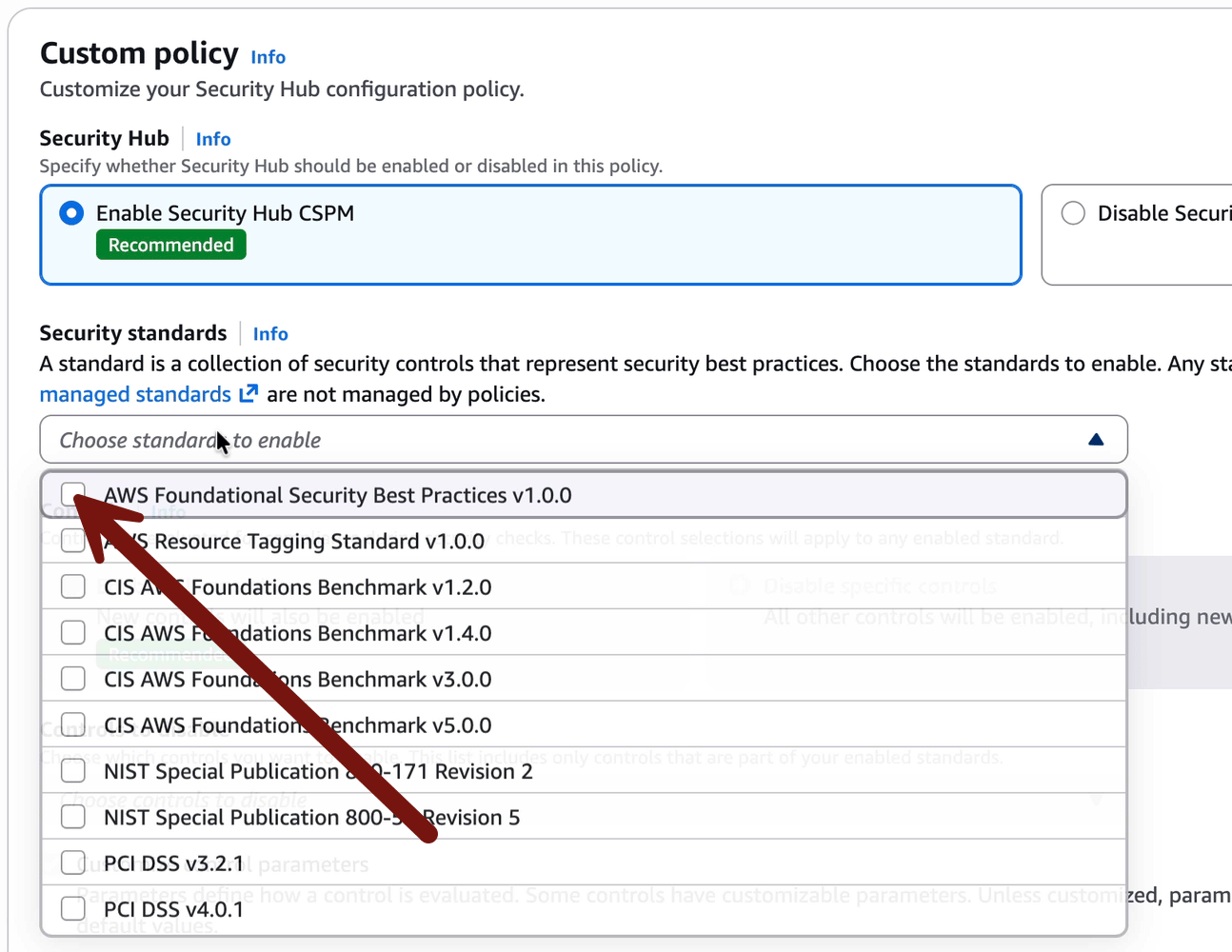
Then Enable all controls and un-check Customize control parameters:
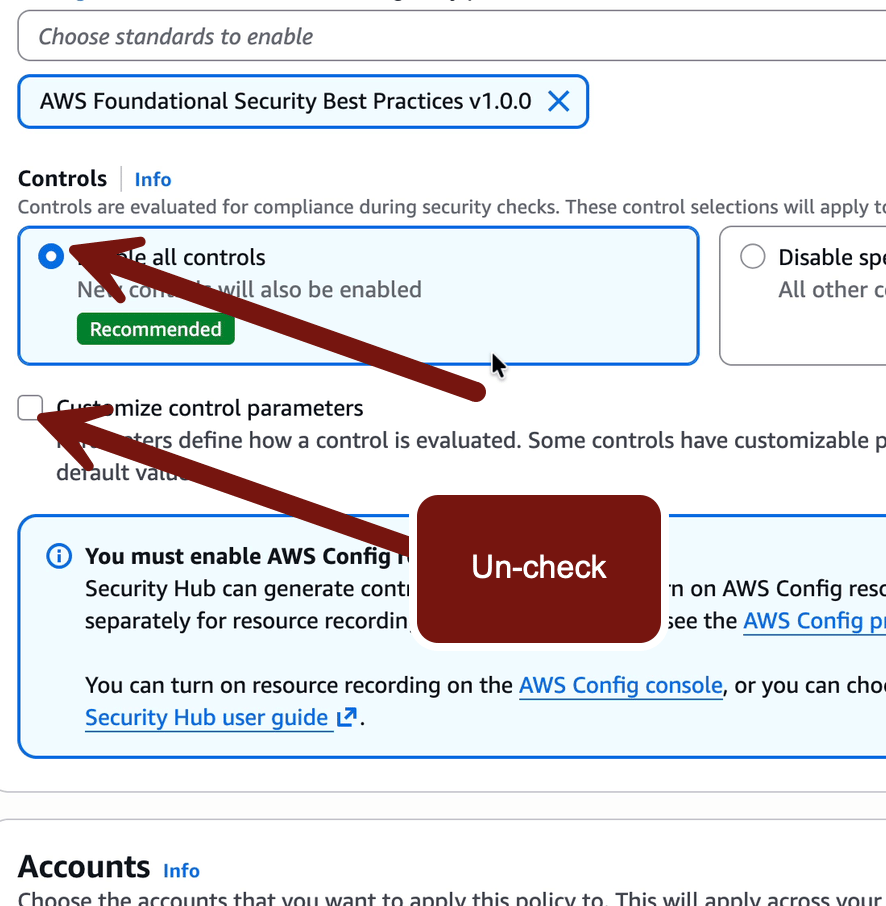
Then Next > Save policy and apply:
This will take a bit to roll out through your accounts, but it is updating everything to start collecting EVEN MORE CSPM FINDINGS BWAHAHAHAHA!!!!
It takes hours for findings to show up. I left mine running overnight and it found… a lot. Too much, since most of them I don’t care about.
Yes, I do need to know that for compliance, but not always for security. Or maybe it’s only a security issue sometimes. This is the challenge of CSPM, and why we waited.
The new Security Hub attempts to address this by offering some more-focused finding types such as Threats and Exposures. None of these triggered in my account even after running it overnight, but our organization should be in pretty good shape, even though we opened a few things up.

At this point, feel free to click around, look at Resources and Findings, and maybe even see if you can create an exposure finding and see the attack graph. I… ran out of time to write this lab up. :)
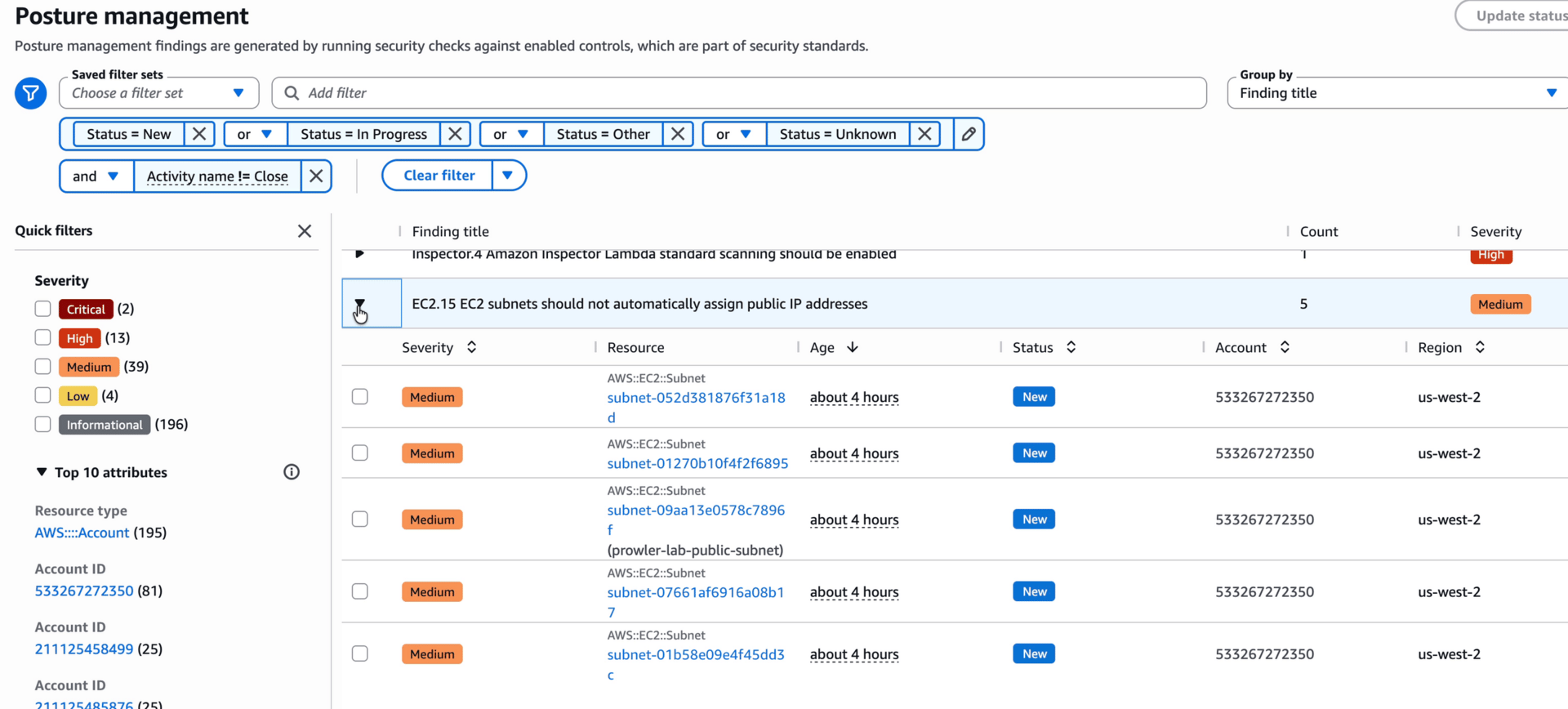
It may take a bit of time for these to show up.
I’d leave it running for a day or overnight, then delete:
Deletion instructions
In SecurityAudit
Go to Security Hub CSPM
Configuration > Policies > check your policy > Edit > delete (click the X) for the Security Best Practices
Save and apply
Go to Security Hub
Configurations > Policies > Default > Disable all regions
This actually prevents Security Hub from being turned on manually anywhere — remember that for the future.
Go to Sign-in portal > CloudSLAW > AdministratorAccess > Organizations and copy your root OU ID (it starts with “r-xxxx”)
CloudFormation > StackSets > Config > Delete stacks from stack set
Enter the root OU
Add all regions
Max concurrent accounts: 10
Failure tolerance: 9
Submit
Then Actions > Delete stack set
That’s it! All Security Hub versions and Config are now disabled.
Lab Key Points
Security Hub is the new security center for AWS and it aggregates, correlates, and prioritizes security information.
Security Hub CSPM is the old version of Security Hub, which now “feeds” posture findings into the new Security Hub.
Our labs all used delegated administration, which we previously configured and had to update.
These services are not free.
-Rich
Reply